“Security Questions” are one of the more or less common mechanisms trying to improve the security of your online account. It’s an easy way to reauthenticate yourself, should you ever lose your password and get locked out of your account. Usually during account registration you not only get to choose your password, you also get to choose your own personal question and an appropriate answer to it. To prevent users from selecting some apparently dumb and easy to guess question (for example: “What color is the sky?”), they typically can choose from different options.
In case you get locked out of your account, present your personal “Open Sesame” and gain again access to reset your password. You might have to prove owning or having access to the e-mail address you registered your account with, but there are often other channels to bypass additional checks. Customer hotlines are one of the examples for this.
Examples from the Deutsche Bahn App
“Security Questions” are also called “Shared Secrets” which is a form of static knowledge-based authentication (KBA). Sharing something secret might not sound like a good idea, but it has to be something only you know to keep access to your account secure, right?
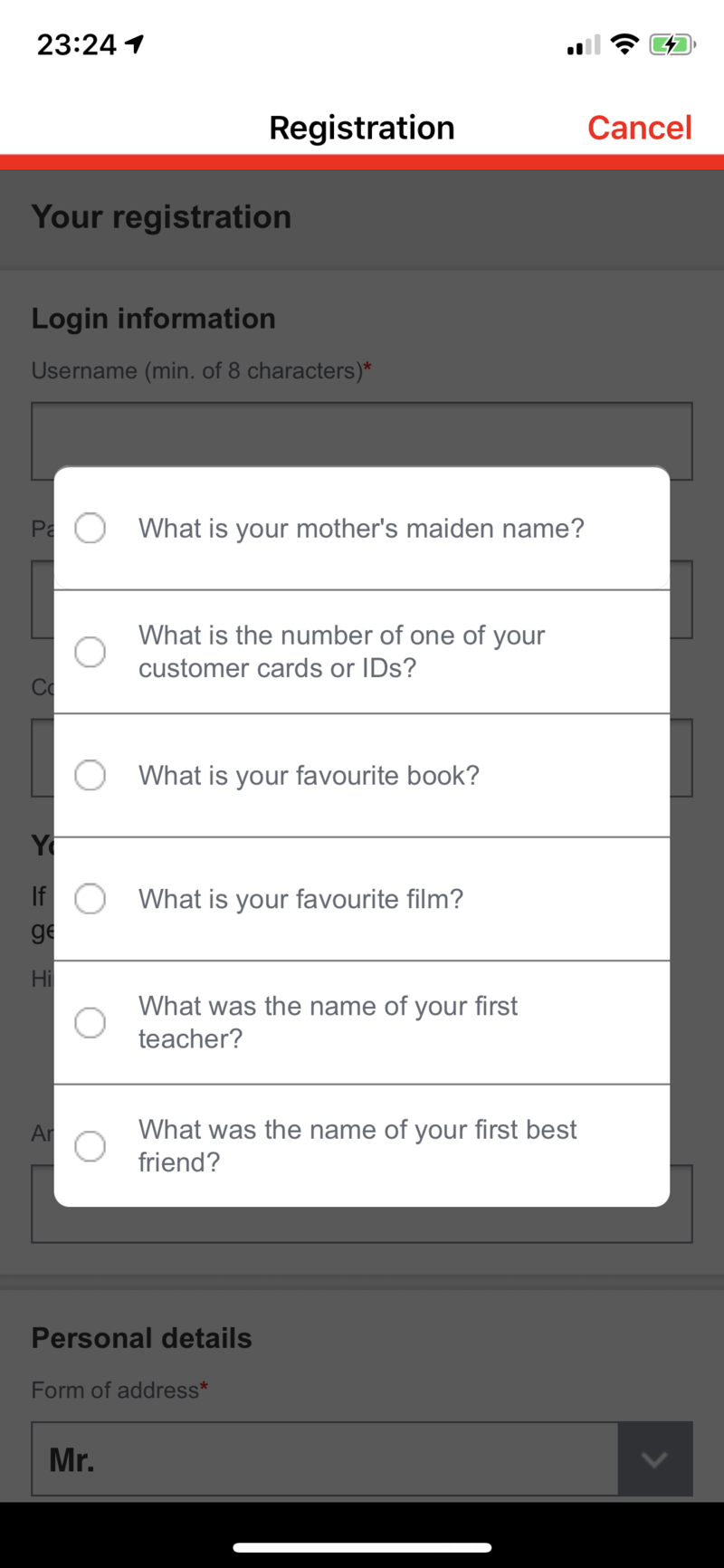
Here are the questions Deutsche Bahn lets you choose from:
- What is your mother’s maiden name?
- What is the number of one of your customer cards or IDs?
- What is your favorite book?
- What is your favorite film?
- What was the name of your first teacher?
- What was the name of your first best friend?
Wait… what?
Let’s have a closer look
I’m pretty sure we can skip figuring out a favorite book or film. We live in a world where you get achievements for completing your social media profile, have some ask-me-anything-via-twitter-aaS and leave a lot of traces in the world wide web.
It might be pretty easy to figure out a first teacher if you have any kind of online resume or are of course connected to one of the “Did we went to school together” platforms. Sometimes an attacker can connect independent information and link it to you. Who knows that shared secret? You, good friends, your school, your teachers, everyone of the 25 people you went to school with, their parents, maybe the pupils magazine, maybe some archived newspaper article about the great role you played in theatre class. Maybe you didn’t publish this information anywhere online but the attacker can guess your cohort, your school decides to go fully digital and publishes an alumni list without your knowledge and so on.
You may never answer this question in a conversation, but think of the possibilities of good social engineering? Who knows your mothers maiden name? What about a “lost friend” calling your husband or wife, pretending to search for someone? Will they correct a caller if he mentions a wrong name? If you look at a large user base, how likely is it that an attacker can simply guess the most common surnames? According to Wikipedia the most common German Surnames are Müller, Schmidt, Schneider, Fischer, Weber, Meyer*, Wagner, Schulz, Becker and Hoffmann. At least five of them match for people in my circle of friends. Attackers might not even target especially you, they could be just be out for fishing.
A special note about using numbers from “customer cards or IDs”: Using something like the number of your ID is a pretty bad idea. This information is sometimes used to identify you and should be handled carefully, like a credit card number for example. The difference is that credit card numbers are usually handled according to PCI DSS requirements and not stored in plaintext fields which can be revealed by yourself or the support staff member on the hotline. Besides that, remember the Marriott / Starwood Security Incident)?
Marriott believes that approximately 5.25 million unencrypted passport numbers were included in the information accessed by an unauthorized third party. The information accessed also includes approximately 18.5 million encrypted passport numbers.
And yes, in the German version, they call it “Ausweis”, which is usually your passport.
If your data was leaked through the Ashley Madison breach, “data” means also your security questions and answers.
Being a smartass about the answers
You might have thought of something super super secret you are sure nobody will ever guess as your secret answer. Maybe you even made it up, used a book which doesn’t exist or secretly renamed your mother.
Lucky you, but that’s not the point. The question is if this a good practice which increases security or if this a bad practice which decreases security. It’s not about the one single smart user, it’s about the pattern itself and its usefulness in the broad field.
Beside that, making things up or even answering with random garbage is like having a second password. Are you sure you will remember it in case you lost your password after some time? If not, you would have to store it in safe place, maybe a password manager. If you have a password manager you could also store the original password in there.
What does the NIST say? 🦊
The National Institute of Standards and Technology (NIST) is an US federal agency providing standards, guidelines and best practices around several topcis, IT security included. Besides some questionable ties to the NSA (see “What NSA’s influence on NIST standards means for feds and the debate around SP 800-90) it definitely makes sense to consider their recommendations.
NIST issues regularly “Special Publications” and around ~ 170 papers prefixed with 800- are focused on computer security.
The SP-800-63 Digital Identity Guidelines focuses among other things on the problem of claiming a virtual identity by linking your real-world identity to it. This comes in different levels and is called Identity Assurance Level. Linking your real-world identity without physical presence, which is what one would try to achieve by security questions, is called IAL2. They are a way to verify a knowledge based secret (KBV), so we can look up the recommended requirements of SP-800-63 5.3.2 Knowledge-Based Verification Requirements. Some of the mentioned requirements are:
b. The CSP SHALL require a minimum of four KBV questions with each requiring a correct answer to successfully complete the KBV step.
c. The CSP SHOULD require free-form response KBV questions.[..]
g. The CSP SHOULD NOT ask the same KBV questions in subsequent attempts.
i. The CSP SHALL NOT use KBV questions for which the answers do not change (e.g., “What was your first car?”).
So, minimum of 4 questions, free-form, not ask the same questions in subsequent attempts, no static answers. None of the questions qualify for this subset of the guideline. They are still not a good idea, but at least you should implement them by the recommendations, if you have to. Sounds like a horrible UX experience, but United Airlines roled those out in 2016 and also people over at the UX-Wonder-Factory Apple.
Since these guidelines can get quiet long and complicated NIST maintains a FAQ for some of them. The FAQ for SP-800-63 contains two question about the topic:
- Is use of knowledge-based authentication permitted?
- Is it permissible to use sets of questions and answers stored by the subscriber for password reset?
Short answer, no:
Knowledge-based authentication, where the claimant is prompted to answer questions that are presumably known only by the claimant, also does not constitute an acceptable secret for digital authentication.
KBA for password reset would leave the account vulnerable to takeover. Alternative authenticators for password reset include lists of look-up secrets and out-of-band device authentication.
But do they really leave your account “vulnerable to takeover”? Let’s see…
Other Research and examples where Security Questions screwed people over
There was some research conducted by Stuart Schechter A.J. Brush and Serge Egelman at Microsoft resulting in a paper “It’s no secret - Measuring the security and reliability of authentication via ‘secret’ questions (PDF)”. Quoted directly from the conclusion of the paper:
The security of personal questions appears significantly weaker than passwords. Acquaintances with whom participants reported being unwilling to share their Hotmail passwords were able to guess 17% of answers. For our geographically-homogenous sample, 13% of answers could be guessed by iterating through the five most popular answers of other users. Userwritten questions were no better: roughly half were vulnerable to guessing by either acquaintances or those who had never met the account holder.
Btw. following their own advice may have had spared them a Talk at 2018 Blackhat: When everyone’s dog is named Fluffy - Abusing the brand-new security questions in Windows 10 to gain domain-wide persistence (PDF Blackhat Slides).
If still in doubt, here is a selection of cases which gained a more ore less broader audience, involving “Security Questions”:
- Slate: Paris Hiltons T-Mobile Account and her favorite’s pet name (2005)
- Wikipedia: Sarah Palin’s E-Mail Account (2008)
- LA Times: Have they no Seamus? Tipster claims hack of Romney email (2012)
- Wired: Time to Kill Security Questions—or Answer Them With Lies (500 million yahoo accounts with questions)
- KasperskyLabs: How I hacked my Apple ID security questions
Conclusion
Stop using them, use better alternatives like mentioned by the NIST: A pre-defined list of emergency recovery codes or out-of-band communication like a SMS. If you have to implement them, do it according to the SP-800-63 requirements.
What better closing then a quote of Bruce Schneiers essay “The Curse of the Secret Question”:
Passwords have reached the end of their useful life. Today, they only work for low-security applications. The secret question is just one manifestation of that fact.
