The purpose of a Threat Modelling
Building a system invites of hundreds of possible attack vectors which can even be chained together. The more complex your system gets and the more components your system has, the more vectors you get. The OWASP Top 10 give a glimpse at the top of the iceberg and how diverse these threats are. Usually by gaining experience people tend to mitigate more and more of these threats during the creation of a system. Some of the vectors might be easy to spot (e.g. lack of authentication) and some might be harder to find (chained injection attacks combined with social engineering). For all of them you have to decide if they are in scope or an accepted risk. From all these vectors we need to pick the right ones and apply mitigation techniques to our system. We have to pick because we are usually limited by time and/or budget. Threat Modelling is a tool for finding threats and documenting your mitigations. It helps you to keep focus and invest your time on the right place.
A threat model by itself is not defined standard. The form should heavily depend on the audience and can be a written list of paragraphs like Vault’s Security Model Documentation or an list of thousands of questions and answers about your system, to be presented to regulators.
A popular method is to describe your system with a data flow diagram and try to pin STRIDE oriented threats on the different components. You would then prioritize and act accordingly.
STRIDE is a mnemonic of Spoofing, Tampering, Repudiation, Information disclosure, Denial of service and Elevation of privilege and was created as a framework at Microsoft. See the original publication “The threats to our products” in this wonderful docx file.
Little and often
The motivations behind threat modelling can vary a lot. Sometimes you find software projects which have created a giant threat model, maybe with support of a security specialist and that’s it. Giant data flow diagram, hundreds of threats, buried deep in a wiki or special tooling. Most of the time, you won’t get any more secure software with this approach. It might even annoy everyone having to create or work with it.
Like Jim Gumbley explained in “A Guide to Threat Modelling for Developers” why it is so important to start threat modelling ‘little and often’. As mentioned, systems are complex things, so we want to break down their complexity during analysis. Little at a time but focused. Systems change and threats change so this adds the need to do this on a regular basis and it’s much easier with smaller units.
Finding threats for a system can be crossing out points on a check list but may also be more like a brainstorming session. This might be easy with a “security mindset” background but the real-world knowledge of the system is usually with the people creating and maintaining it.
To allow a better access to the threats and boost your creativity a little bit, Adam Shostack created the card game “Elevation of Privilege”. It consists of 78 STRIDE cards which can be applied to your prior created data flow diagram. The game design is influenced by serious play principles and focuses on getting actionable items at the end.
The game is nicely illustrated, shared under CC-BY-3.0 and can be downloaded for free. Don’t get distracted by the Microsoft advertisement on 80% of the page.
Elevation of Privilege with its 78 cards is a nice adaptation of Tarot.
The Tarot Card Game
Tarot card decks evolved from adding additional trump cards to the playing cards arriving in Europe in the 14th century. Over decades a lot of regional card decks and playing variants emerged and some of them are still played today, for example the French-tarot played with the Tarot Nouveau card deck or Cego played with the Tarock deck.
Fortune telling using the tarot decks was popularized during the 18th century. The colorful illustrated trump cards made it easy to build up a esoteric system around them. The trump cards (or great Arcana) are illustrated around the Hero’s Journey narrative, therefore they are a perfect fit for complex story telling. Other attributions, like an ancient Egypt origin are not backed by any facts and seem more like a magic powder added on top by different mystics.
It got another popularity boost by the publication of the Waite/Smith deck by Rider (a part of Penguin Public House today) around 1910 and the Thoth deck by Crowley/Harris in the 1940s, both still in use today.
Using Tarot as entropy input
Tarot cards can not only be used for esoteric fortune telling but also as a tool for random input. My colleague @mkhl did write a perfect short summary of that:
And I think random input is underappreciated and can help break out of cycles. The value can be in receiving random input, relating it to yourself, and using that to observe something about your internal state you might not otherwise had access to. (@mkhl on twitter)
Software development usually consists of repeating cycles and ceremony, be it a simple code-and-evaluate loop or a more formalized process like scheduled development cycles with fixed retrospectives. Sometimes you may find yourself stuck inside your focused area and like going for a (virtual) walk or rubber duck debugging can free your thinking, drawing a tarot card, trying to relate it to your problem may also be of help.
For example, if this isn’t a wonderful visualization of destroying the monolith, I don’t know:

Threat Model card of the day
In Tarot there is a simple drawing technique called “Card of the day”. You draw a card before or after your day starts and follow your thoughts around it. This matches perfectly with the principle of “many small threat modelling sessions over time are better than one big threat model”.
Switch the Tarot deck with Adam Shostack’s Elevation of Privilige Card game and you get your daily threat modelling inspiration. Discuss the card, try it to apply it to your system, maybe file a bug or document it as an accepted risk.
Add it to your daily routine, weekly development cycle or simply from time to time.
Remember to have fun :)
The Threat Oracle
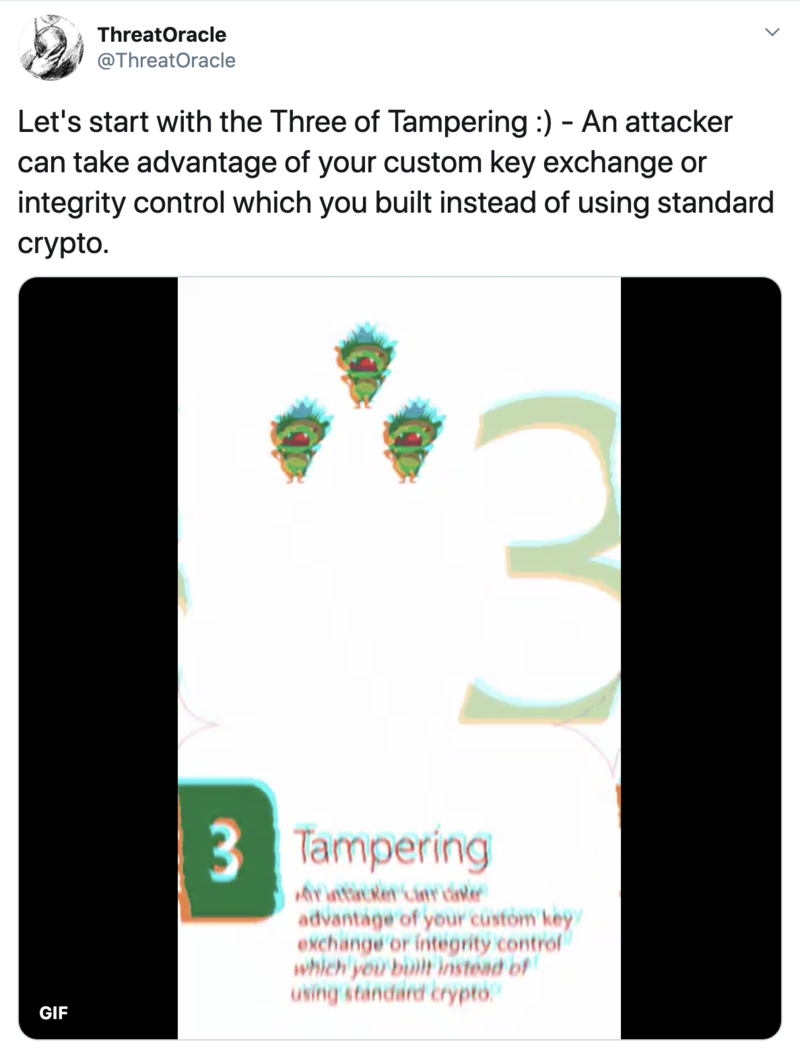
Since the future is today, you don’t have to visit any strange fortune tellers trailer, you can get your Tarot cards drawn by friendly and strange Twitter bots.
The same is now possible for Daily Threat Modelling card. Beware of the mighty @ThreatOracle 🐦.
It’s your daily reminder of the evil out there in the interwebs. Currently it draws a card a day from a glitched up version of the Elevation of Privilege deck. No need for manual shuffling and picking cards. Extending it to the Privacy Suite and adding the OWASP Cornucopia deck is work in progress.